Key Insights
- Breaking News: Silver Fox APT is weaponizing DeepSeek AI installer downloads as a social engineering vector to compromise Taiwanese government and technology sector systems with Gh0stRAT malware.
- Impact: The campaign demonstrates how threat actors are exploiting legitimate AI tool adoption trends to infiltrate critical infrastructure, raising urgent concerns about supply chain security across the Asia Pacific region.
- The Numbers: Silver Fox has expanded operations from initial China and Taiwan targeting to Japan and Malaysia, with multiple malware families including Winos 4.0, HoldingHands RAT, and now Gh0stRAT variants in active circulation.
The Threat Is Real. And It’s Using Your Favorite AI Tool.
Taiwan’s cybersecurity landscape just shifted. A sophisticated campaign is weaponizing one of the year’s hottest AI tools—DeepSeek’s large language model—to infiltrate government agencies and technology firms across the island. This isn’t theoretical. It’s happening now.
The campaign, suspected to be orchestrated by Silver Fox APT (also tracked as Void Arachne), represents a critical inflection point in how state-sponsored threat actors operate. They’re no longer just sending generic phishing emails. They’re exploiting genuine user behavior—the rush to adopt cutting-edge AI solutions—to gain persistent access to sensitive systems.
Why does this matter? Because it works. And because it signals a troubling trend:
The faster technology adoption accelerates, the faster threat actors weaponize it.
How the Silver Fox’s Deepseek Attack Works ?
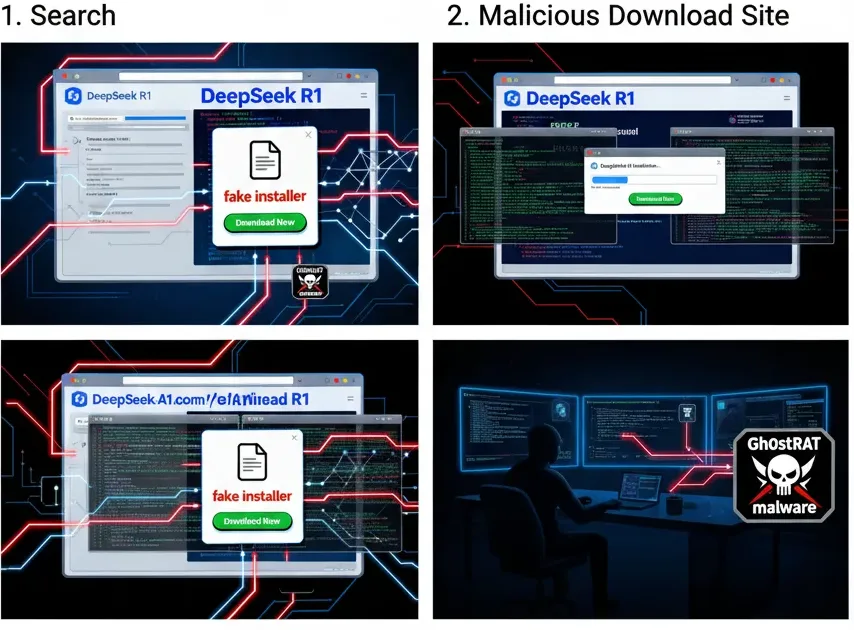
The mechanics are deceptively simple, yet highly effective. Victims receive phishing emails or encounter spoofed websites that appear to host legitimate DeepSeek R1 installer files. The fake landing pages mimic authentic DeepSeek distribution channels with convincing detail. When users download what they believe is the AI tool, they’re actually executing a malware loader.
Once executed, the payload deploys Gh0stRAT—a remote access trojan derived from the Gh0st RAT source code that leaked publicly in 2008. This malware grants attackers complete remote access to infected systems. From there, they can steal data, establish persistence, and conduct long-term espionage operations.
The sophistication lies in the social engineering layer. DeepSeek has gained massive traction in Taiwan and across Asia as organizations race to integrate AI capabilities. This creates a window of opportunity. Users are motivated to download. Security awareness is lower for “legitimate” software. The attack surface expands exponentially.
Silver Fox’s Expanding Arsenal
This DeepSeek campaign is part of a broader escalation by Silver Fox. The group has been actively targeting Taiwan since early 2024, deploying multiple malware families in coordinated campaigns.
Previous operations have utilized Winos 4.0 (also called ValleyRAT) in phishing emails impersonating Taiwan’s National Taxation Bureau. The group has also deployed HoldingHands RAT (tracked as Gh0stBins) against targets in Japan and Malaysia. More recent activity has leveraged fake websites advertising popular software like WPS Office, Sogou, and now DeepSeek to distribute Sainbox RAT and the Hidden rootkit.
The pattern is clear: Silver Fox adapts its lures to match trending software and services. They’re not static. They’re reactive. They’re learning what works.
Taiwan’s government and industrial sectors have been hit particularly hard. Healthcare organizations have faced targeted intrusions exploiting vulnerabilities in Philips DICOM medical imaging software. The “power and energy sector has experienced potential disruptions.” Large-scale logistics and transportation networks have been compromised. These aren’t random attacks. They’re strategic targeting of critical infrastructure.
The Geopolitical Dimension of Silver Fox’s Attack
Silver Fox’s focus on Taiwan is not accidental. The group is believed to be state-sponsored and operates with clear geopolitical motivations. Researchers have documented that the group primarily targets Chinese-speaking users and Taiwanese organizations, with operations extending to Japan, Malaysia, and China itself.
The intelligence collection appears designed to weaken Taiwan’s economy and security posture. By compromising government financial systems, industrial networks, and healthcare infrastructure, the group gains visibility into Taiwan’s strategic vulnerabilities. This is espionage with a purpose.
You Would Love To Read: Taiwan’s 14-Year Sentence Exposes Chip Espionage Crisis
The use of advanced evasion techniques—including disabling antivirus software with vulnerable drivers, VMProtect obfuscation, and language-specific targeting—underscores the technical sophistication behind these operations. This isn’t script-kiddie activity. This is a well-resourced, organized threat actor.
Why AI Adoption Creates New Risk ?
The DeepSeek lure represents a critical vulnerability in how organizations approach emerging technology adoption. When new tools gain rapid popularity, security protocols often lag behind user demand.
Employees are incentivized to download and experiment. IT departments struggle to keep pace with vetting and deployment.
Threat actors exploit this friction. They understand that security teams are overwhelmed. They know that users are eager to adopt the latest tools. They weaponize this gap.
For Taiwanese enterprises and government agencies, this campaign is particularly significant because it demonstrates how legitimate AI tool adoption can become a vector for compromise. Organizations that are rapidly integrating DeepSeek or similar LLM tools into their workflows are now operating in an elevated threat environment.
The supply chain security implications are profound. If an organization’s endpoint is compromised through a fake AI installer, attackers gain access to all downstream systems connected to that endpoint. A single compromised developer machine could expose proprietary AI models, training data, or strategic technology roadmaps.
Detection and Response Challenges for AI attacks.
Gh0stRAT and its variants are particularly challenging to detect because they’re based on publicly leaked source code that has been widely modified and distributed. Signature-based detection becomes less effective when the malware family has hundreds of variants in circulation.
The multi-stage infection process compounds the challenge. Initial payloads are often lightweight and benign-looking. The actual malware is downloaded and executed in memory, leaving minimal forensic artifacts on disk. DLL side-loading techniques further obscure the attack chain.
Organizations need to implement behavioral detection systems that can identify suspicious process execution patterns, unusual network connections, and privilege escalation attempts—not just known malware signatures.
What Organizations Should Do Now ?
For Taiwanese enterprises and government agencies, immediate action is required:
- Email Security: Deploy advanced email filtering that can detect phishing campaigns impersonating software vendors. Train employees to verify download sources independently, never clicking links in unsolicited emails.
- Endpoint Protection: Implement endpoint detection and response (EDR) solutions that can identify suspicious process execution and lateral movement. Monitor for indicators of compromise associated with Gh0stRAT and related malware families.
- Supply Chain Verification: When adopting new software tools, verify downloads directly from official vendor websites. Use cryptographic signatures to validate installer integrity. Never rely on third-party distribution channels.
- Zero-Trust Architecture: Assume that endpoints may be compromised. Implement network segmentation to limit lateral movement. Require multi-factor authentication for all critical systems.
If you’re tracking these threats and want to stay ahead of emerging campaigns, consider joining the WireUnwired Research community. Connect with security professionals analyzing Silver Fox and other APT groups on LinkedIn or WhatsApp for real-time threat intelligence and analysis.
The Broader Picture
Silver Fox’s DeepSeek campaign is not an isolated incident. It’s part of a sustained, sophisticated effort to compromise Taiwan’s critical infrastructure and steal strategic intelligence. The group has demonstrated adaptability, technical sophistication, and clear geopolitical motivation.
What makes this campaign particularly noteworthy is its timing and targeting precision. DeepSeek’s rapid adoption in Taiwan created a window of opportunity. Silver Fox recognized it and exploited it. This is threat actor behavior at its most effective: opportunistic, yet strategically focused.
For the broader cybersecurity community, the lesson is stark. Emerging technology adoption creates emerging attack surfaces. The faster organizations move to integrate new tools, the faster threat actors move to weaponize them. Security must be embedded into adoption workflows from day one, not bolted on afterward.
Taiwan’s government and private sector face a critical juncture. The threat is real. The capability is demonstrated. The motivation is clear. The time to act is now.
Discover more from WireUnwired Research
Subscribe to get the latest posts sent to your email.